Ransomware has become one of the most dangerous threats in the digital landscape, affecting businesses, governments, and individuals alike.
Ransomware has become one of the most dangerous threats in the digital landscape, affecting businesses, governments, and individuals alike. It is a type of malware that locks or encrypts your data, demanding a ransom to restore access. Falling victim to ransomware can result in financial loss, operational disruption, and significant reputational damage.
To mitigate these risks, it is essential to understand how to solve ransomware effectively. This article explores the nature of ransomware, its impact, and actionable solutions to prevent, detect, and recover from attacks.
Understanding Ransomware
1. What is Ransomware?
Ransomware is a malicious program designed to encrypt files or lock systems, making data inaccessible until a ransom is paid. There are several types of ransomware:
- Crypto Ransomware: Encrypts files, making them unusable until decrypted.
- Locker Ransomware: Locks the entire system, preventing access to any part of it.
- Scareware: Fakes alerts demanding payment to fix nonexistent issues.
- Double Extortion Ransomware: Threatens to leak sensitive data publicly if payment isn’t made.
Understanding these types is the first step to effectively solve ransomware incidents.
2. How Ransomware Spreads
Ransomware often enters systems through:
- Phishing emails and malicious attachments
- Compromised websites or downloads
- Remote Desktop Protocol (RDP) vulnerabilities
- Software or system security flaws
By recognizing these attack vectors, organizations can focus on prevention strategies.
The Impact of Ransomware
1. Financial Loss
Ransom payments, downtime, and recovery costs can result in significant financial burdens. The global average ransom payment has risen dramatically over recent years, highlighting the severity of these attacks.
2. Data Loss
Without proper backups, ransomware can permanently destroy critical files, affecting business continuity.
3. Operational Disruption
Systems locked by ransomware can halt productivity, delay projects, and affect client services.
4. Reputational Damage
Data breaches and ransomware incidents can erode trust among customers, clients, and stakeholders.
To solve ransomware, organizations must implement proactive strategies to minimize these consequences.
Effective Methods to Solve Ransomware
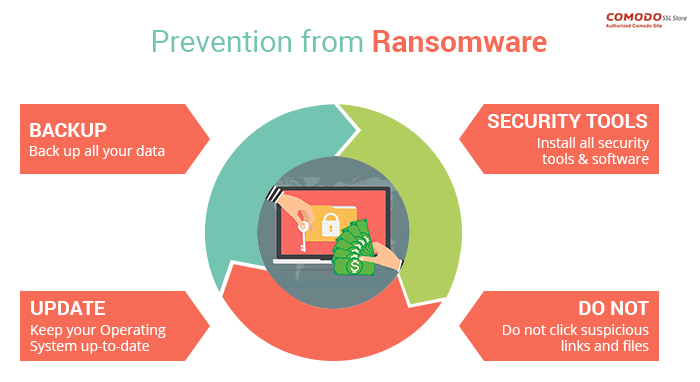
1. Maintain Regular Backups
The most reliable way to mitigate ransomware damage is by keeping frequent and secure backups. Best practices include:
- Using offline or offsite backups
- Employing cloud backup solutions with versioning
- Regularly testing backups for integrity
Reliable backups allow organizations to restore systems without paying the ransom.
2. Deploy Endpoint Security
Comprehensive endpoint protection is crucial. Features should include:
- Real-time malware detection
- Behavioral analysis to identify suspicious activity
- Automatic quarantine and removal
Endpoint security forms a vital layer in any strategy to solve ransomware.
3. Network Security Measures
Securing your network can prevent ransomware from spreading. Measures include:
- Firewalls and intrusion detection systems
- Segmenting networks to isolate sensitive data
- Applying regular patches and updates to software and systems
A robust network defense reduces the chances of widespread infection.
4. Implement Email Security
Since ransomware often spreads via email, strong email security is critical:
- Advanced spam filters and malware scanners
- Attachment and link scanning
- Employee training to identify phishing attempts
Email security, coupled with awareness, forms a strong preventive layer.
5. Educate Employees
Human error is a major cause of ransomware success. Training employees to recognize threats and follow safe practices helps prevent infections.
Topics should include:
- Identifying phishing emails and suspicious links
- Avoiding unverified downloads
- Reporting potential security incidents immediately
Education is an essential part of any effort to solve ransomware effectively.
6. Monitor and Detect Threats
Continuous monitoring and threat intelligence can help detect ransomware early. Recommended practices:
- Network activity monitoring for unusual behavior
- Real-time alerts for suspicious file changes
- Utilizing threat intelligence feeds for emerging ransomware variants
Early detection minimizes damage and speeds up recovery.
7. Apply Multi-Factor Authentication (MFA)
MFA adds an extra layer of security, making it harder for attackers to access accounts even if credentials are compromised. MFA is highly effective in reducing ransomware vulnerabilities.
Steps to Recover and Solve Ransomware Attacks

1. Containment
If a ransomware attack occurs, immediately isolate affected systems to prevent further spread. Disconnect infected devices from networks and cloud systems.
2. Identify the Ransomware
Understanding the specific ransomware strain can help determine whether a decryption tool or method is available. Resources such as cybersecurity databases may provide solutions for known ransomware variants.
3. Restore from Backup
Once containment is achieved, restore data from secure backups. Verify that restored systems are free of malware before reconnecting them to networks.
4. Avoid Paying Ransom
Paying ransom does not guarantee data recovery and may encourage further attacks. Focus on recovery strategies that do not involve giving money to attackers.
5. Post-Attack Analysis
After recovery, perform a detailed analysis to understand how the attack occurred. Update security policies, patches, and employee training to prevent future incidents.
Advanced Strategies to Solve Ransomware

1. AI and Machine Learning
Artificial intelligence can analyze behavior patterns to detect ransomware before encryption occurs. Machine learning algorithms can predict attacks and respond proactively.
2. Cloud Security Solutions
Cloud-based security solutions offer centralized threat detection, backup, and recovery options. Cloud providers often include ransomware-specific protections to minimize impact.
3. Zero Trust Architecture
Zero trust models require verification for every user and device attempting to access network resources. Implementing zero trust reduces the attack surface for ransomware.
4. Incident Response Planning
A detailed response plan ensures that teams know their roles during an attack. Having predefined procedures reduces response time and mitigates damage.
Conclusion
Ransomware is a growing threat that can cause significant disruption and financial loss. To solve ransomware, organizations must adopt a multi-layered approach combining prevention, detection, and recovery.
Key strategies include maintaining secure backups, implementing endpoint and network security, educating employees, applying MFA, and leveraging advanced technologies like AI and cloud security. In the event of an attack, quick containment, proper identification, and recovery from backups are critical to minimizing damage.
By prioritizing robust cybersecurity measures and proactive planning, businesses can effectively solve ransomware, protect critical data, and ensure long-term operational resilience in the face of evolving digital threats.


COMMENTS